HUMAN FACTOR IN CYBERSECURITY
According to the Verizon Data Breach Investigations Report, 68% of successful cyberattacks worldwide were facilitated by user negligence or lack of preparedness. In Italy, this percentage is 57%, but given current trends and recent statistics, this number is expected to rise due to the increasing complexity of these attacks, which exploit social engineering techniques.
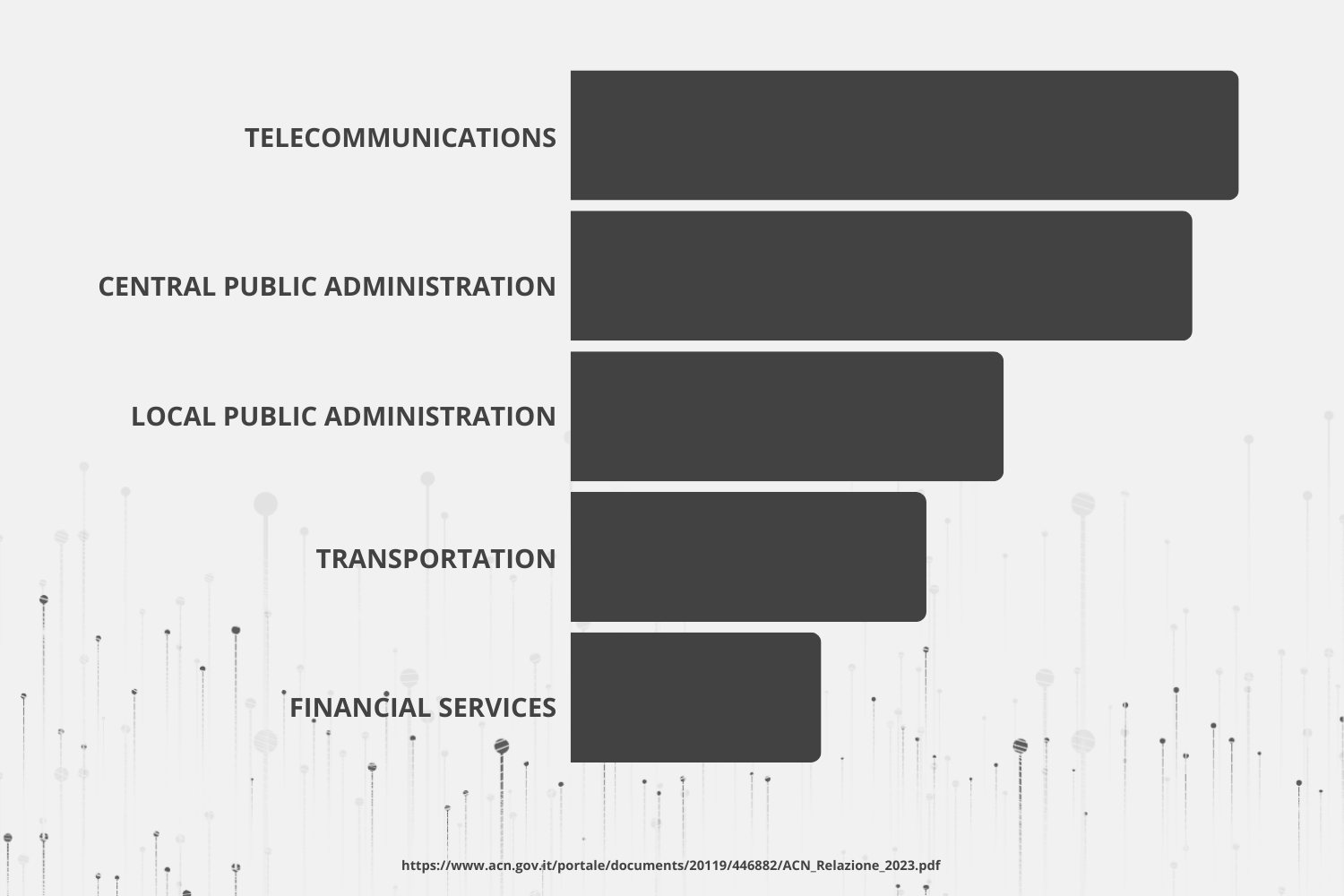
In 2023, the sectors most affected in Italy, according to data from the Agenzia per la Cybersicurezza Nazionale (ACN), were:
These sectors are particularly targeted due to their strategic importance and the vast amount of data they manage. The public administration is a primary target for international cybercriminal groups, who aim to access national critical systems to steal sensitive and confidential data. News stories have shown that, globally, hackers have often been able to keep these backdoors active for extended periods, allowing them to maximize the impact of their attacks.
All sector research and data analysis clearly indicate that employees and business collaborators can represent both a vulnerability and a strategic resource for data protection and safeguarding technological infrastructures.
To address this challenge, Cinetix, in collaboration with specialized partners, offers advanced and interactive cybersecurity training programs, access control solutions, and innovative technologies for in-depth analysis of cyberattack risks, with the goal of transforming employees into the first line of defense against cyber threats.
Thanks to our experience and our network of specialized partners, we offer:
- Field training: practical tools to quickly recognize attacks using social engineering techniques, such as phishing, business email compromise, and smishing.
- Specialized cybersecurity consulting: analysis of the existing corporate IT infrastructure and targeted solutions for its optimization.
- Customized learning programs: tailored courses for employees with varying levels of experience and business roles, ensuring everyone acquires the necessary skills.
- Access control solutions: software that allows real-time monitoring of access to corporate resources, reducing the risk of intrusions and preventing data exfiltration.
- Penetration test: Application of innovative methodologies to identify specific vulnerabilities and assess their potential impact on IT systems in case of compromise.
The result of these initiatives is a comprehensive protection strategy, combining advanced technological defenses and employee awareness for 360-degree security.